Cndnsd Vrsn: 4 PM Thursday May 10th ACS Room 123- XML Update
The next meeting of the Front Range UNIX Users Group (FRUUG) will be held at
4:00 P.M. on Thursday May 10th.
In the three years since its definition, XML itself
has not changed at all. However, there is an ongoing
deluge of XML applications and related technologies.
Our May 10 meeting will present an overview of several
topics, like XSLT, XSLFO, SOAP, XP, Schema, XPointer,
XPath, RDF, DOM1,2,3, SAX1,2, JDOM, XHTML, etc.
The speaker? You, hopefully!
We are soliciting speakers to give short, five-minute presentations
on their practical experience using XML or other XML-related technologies.
Mark Carlson and Tom Cargill, FRUUG Executive Committee members, are
preparing brief presentations and are coordinating volunteers.
So far, we have four additional speakers signed up to present
their work at this meeting:
- Uche Ogbuji, from FourThought: RDF
- Jim Morgan, Freshwater Software: Crimson/Xalan
- Tom Poindexter, Talus Technologies: XML/RPC
- Mike Olsen, FourThought: SOAP
To participate, please send an e-mail to mac at fruug.org or
cargill at fruug.org (at signs removed to prevent spamming)
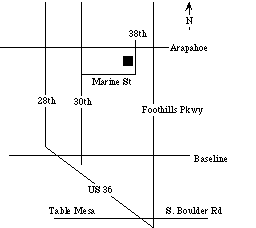
This meeting will be in room 123 of
the CU Academic Computing Center building at Arapahoe and Marine Streets in
Boulder. Marine St intersects Arapahoe at 38th St; the Computing Center is
on the southwest corner.
This month marks the 20th anniversary of FRUUG's first meeting
in April 1981. Now that FRUUG is no longer a teen-ager, we
prepared a little writeup that talks about some of our
history and where we've been right on top of new technical
innovations-- and some embarrassing places where we weren't.
Have a look at
http://www.fruug.org/about/birthday.html and see what meetings you remember.
During our 20th birthday year, we'd like to get all of our old
meeting announcements converted from old formats and put into
our meeting archive. Please contact us if you'd like to
volunteer to help.
At our March meeting, Evi Nemeth
of the University of Colorado,
XOR,
and the Cooperative Association for Internet Data Analysis
(CAIDA)
presented her most recent work measuring traffic to the Internet's DNS
root servers, their performance, and problems in the DNS structure.
Evi's work involved two sets of measurements. At the University
of California, San Diego, she was able to use an optical splitter
to monitor all DNS client traffic from the university to the
various root servers. Her optical splitter "takes only five percent
of the light and 100 percent of the data." From this perspective,
she was able to monitor performance of all the root servers queried
from anywhere in the university, easily finding out which servers
have problems, and in some cases helping the root server administrators
to improve their performance. Evi shared with us her observations
of "who's been naughty and who's been nice."
At the F root server, Evi managed to spend some time collecting
6 GB per hour of trace data and gaining a perspective on performance
from the root server's perspective. More interesting than the
performance information she presented was the shocking fact that
25 percent of the queries the servers received were bogus,
highlighting the magnitude of the problem with software bugs
and DNS server mis-configurations.
She spent a significant amount of time categorizing the bogus queries,
and showing how the bogus queries increased when a new version
of Microsoft Windows were released-- and even tracking down a
missing 'else' in their code that prevented their DNS server from
ever caching responses to their queries. Some of the
queries included ones with unroutable source addresses (like 10.1.1.1),
queries asking for reverse lookups of private addresses,
queries asking: "what's the IP address of 192.168.10.1," and
queries with spoofed source addresses that were used as part
of the denial-of-service attacks last winter.
Evi tracked down many of these problems to bad default configurations
in Windows; but to be fair she tracked down quite a few to UNIX
operating system-hosted DNS servers as well.
Evi presented lots of interesting information that we hope to have
on our site soon-- her work is currently submitted for publication
and cannot be published by us before it is accepted. Stay tuned.
Notes and resources from our past meetings are available at
http://www.fruug.org/mtgarchive/index.html.
We're still working on our future meetings schedule, and may have
a June meeting lined up on the ins and outs of the
UNICODE standard.
The search engines have been busily crawling through the
new FRUUG site, and if you have an overdue book your
name may be part of the information indexed. If you have
a book from the FRUUG library, please return it to the next meeting
or make arrangements to return it to us. We don't like to update
our overdue books page, but if we must, we will.
New books from our publisher friends this month include:
From Addison Wesley:
- Applying Use Cases, Second Edition, by Geri Schneider and Jason P. Winters
- Building Parsers with Java, by Steven John Metsker
- Effective Requirements Practices, by Ralph R. Young
- Perl Debugged, by Peter Scott and Ed Wright
- Writing CGI Applications with Perl, by Kevin Meltzer and Brent Michalski
From The USENIX Association:
- Proceedings from the 6th USENIX Conference on Object-Oriented Technologies and Systems (COOTS'01), San Antonio, February 2001.
You may check out books using your business card as your library card;
you must be on the membership list to check books out. Books are due at the
meeting following the one in which they are checked out.
Remember that your FRUUG membership entitles you to
discounts on your book orders
from both New Riders Publishing and O'Reilly & Associates; refer
to the FRUUG Web site for details.




