|
Cndnsd Vrsn: 4 PM Thursday March 15th ACS Room 123- DNS Damage
The next meeting of the Front Range UNIX Users Group (FRUUG) will be held at
4:00 P.M. on Thursday March 15th. Evi Nemeth of the University of Colorado,
XOR, and the Cooperative Association for Internet Data Analysis
(CAIDA)
will present her most recent work measuring traffic to the Internet's DNS
root servers, their performance, and problems in the DNS structure.
The Internet Domain Name System (DNS) is an essential part of the
Internet infrastructure. Each web site or email lookup involves
traversing a tree-structured distributed database to complete the
mapping from a hostname to an IP address. The root and top level domain
name servers form the highest level of authority over the Internet
naming hierarchy, and thus are an essential prerequisite to reaching every
URL or email address we seek. To function properly, name servers must
cache both positive and negative answers (i.e., knowledge of
non-answers) near leaves of the tree. The work
that Evi will present passively measured the
performance of these name servers at the root of the tree system from
the client's viewpoint and from some root name servers.
Client measurements from a university campus capture round trip
time, packet loss and query load to the root servers. Loss rates are
surprisingly high and attest to the robustness of the DNS protocols,
which mask most loss. Measurements at root servers show an astounding
number of bogus queries: from 60-85% of observed queries were repeated
from the same host within the measurement interval; greater than 50% of
the queries were unnecessarily repeated from the same host at least
every minute throughout the interval over some samples. These errors
are categorized and the percentage occurrence of each error is
calculated. At times over
14% of a root server's query load derives from queries that violate the
DNS specification. Denial-Of-Service (DOS) attacks using root servers are
common and occurred throughout the measurement period (7-24 Jan 2001).
Though not targeted at the root servers, DOS attacks often use root
servers as reflectors toward a victim network. Evi contrasts these
observations with those found in 1992 study by Danzig.
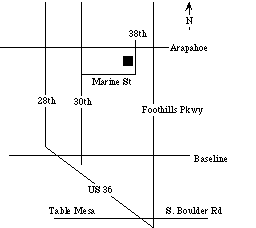
This meeting will be in room 123 of
the CU Academic Computing Center building at Arapahoe and Marine Streets in
Boulder. Marine St intersects Arapahoe at 38th St; the Computing Center is
on the southwest corner.
This year marks FRUUG's 20th birthday, and what better way to
celebrate than to launch our new and improved Web site !
Pay us a visit at http://www.fruug.org
and you'll notice a crisp new appearance, buttons for easy navigation
a site map, and a completely updated meeting archive with announcements
and notes from our past meetings.
Thanks to Heidi Eckert for the great new site design, and to
Steve Gaede for awk, grep, and sedding our old resources
into the new meeting archive.
One feature that you'll like is our FRUUG NEWS
sidebar, which appears on every page and contains any breaking news
of interest to all members.
You can now update your membership information with an on-line form,
and you can enter our first on-line book give-away.
Click on the book giveaway page at
http://www.fruug.org/library/giveaway.html and select the books you'd like to receive.
Enter by March 14, and we'll announce the winners at our meeting.
-
Network Intrusion Detection: An Analyst's Handbook, by
Stephen Northcutt. This is one of the more frequently-recommended
books on intrusion detection.
-
Intrusion Detection, by Rebecca Gurley Bace.
-
UNIX System Administration Handbook, Third Edition, by Evi Nemeth,
Garth Snyder, Scott Seebass, and Trent Hein.
During our 20th birthday year, we'd like to get all of our old
meeting announcements converted from old formats and put into
our meeting archive. Please contact us if you'd like to
volunteer to help.
Thanks to Neal McBurnett, Carl Oppedahl, and Eric Robison
for the stimulating discussion on legal issues affecting
software developers and netizens today.
Notes and resources from our past meetings are available at
http://www.fruug.org/mtgarchive/index.html.
We're still working on our future meetings schedule, and have
a near future meeting lining up on the ins and outs of the
UNICODE standard.
The search engines have been busily crawling through the
new FRUUG site, and if you have an overdue book your
name may be part of the information indexed. If you have
a book from the FRUUG library, please return it to the next meeting
or make arrangements to return it to us. We don't like to update
our overdue books page, but if we must, we will.
Our publisher friends must be hinting that it's time for
a meeting, as we have two titles on XML to add to the
library this month.
From O'Reilly & Associates:
- XML in a Nutshell, by Elliotte Rusty Harold and W. Scott Means
- Learning XML by Erik T. Ray
You may check out books using your business card as your library card;
you must be on the membership list to check books out. Books are due at the
meeting following the one in which they are checked out.
Remember that your FRUUG membership entitles you to
discounts on your book orders
from both New Riders Publishing and O'Reilly & Associates; refer to the FRUUG Web
site for details.

|



